Bringing AI and Blockchain Synergy into Cyber Threat Intelligence Cycle
Bringing AI and Blockchain Synergy into Cyber Threat Intelligence Cycle
Hsia-Ching Carrie Chang and Brady D. Lund
The most critical mission of cybersecurity is to safeguard physical and digital assets to sustain cyber resilience. To accomplish this mission, organizations need to be vigilant about what happens in cyberspace, convert incident data into contextualized information and synthesized knowledge, so sharing cyber threat intelligence becomes important to prevent breach incidents and respond to them in a timely manner. The Multi-State Information Sharing and Analysis Center’s Cyber Threat Intelligence (CTI) team defines threat intelligence as “knowledge about adversaries and their motivations, intentions, and methods that is collected, analyzed, and disseminated in ways that help security and business staff at all levels protect critical assets of the enterprise.” There are three types of threat intelligence, including strategic, operational and tactical intelligence, which aid in decision-making of addressing cyber incidents. While tactical intelligence involves detailed technical issues, guided by strategic and operational intelligence that influence the information sharing between decision maker and security operation team to convert data to synthesized information/knowledge and prioritize operations. CTI plays a pivotal role in governance, risk and compliance (GRC) as it enables risk assessment through the identification of threats, vulnerabilities, compliance requirements, and their consequent impacts. Efficient and secure information sharing matters in effective cyber threat intelligence.
—Efficient and secure information sharing matters in effective cyber threat intelligence—
As artificial intelligence (AI) technologies continue to evolve, the Intelligence and National Security Council (INSA) has engaged with stakeholders to discuss how AI can benefit cyber threat intelligence. According to Center for Internet Security, the intelligence cycle covers five iterative stages: planning (of data collection), collection (from internal or external data sources), processing (data/information), analysis (of data/information), and dissemination, primarily coordinating the efforts from the teams like Security Operations Center (SOC) and Cyber Incident Response Team (CIRT). AI can support the intelligence cycle through two aspects of AI, responsible and explainable AI. However, AI could be susceptible to trust issues and hinder securely sharing intelligence.
 The Economist (2015) considers blockchain as “the trust machine.” Blockchain technology has been initially used in the areas that require trust and security, such as the cryptocurrency like bitcoin, expanded to decentralized financial services, and then applied to a variety of fields that need to share data/information securely, including healthcare, supply chain management, education, cybersecurity, and so on. The trust has been consolidated by different blocks where they use cryptographic techniques (like hashing) to securely connect the chains in order to prevent the records from modifying, thus ensuring the integrity and immutability of data/information exchange. The data/information is transparent within the blockchain network, but data communication/modification requires cryptography for identity verification to protect the data security and privacy. Even so, blockchain needs AI technologies to efficiently process and analyze large volumes of data/information stored in blockchain.
The Economist (2015) considers blockchain as “the trust machine.” Blockchain technology has been initially used in the areas that require trust and security, such as the cryptocurrency like bitcoin, expanded to decentralized financial services, and then applied to a variety of fields that need to share data/information securely, including healthcare, supply chain management, education, cybersecurity, and so on. The trust has been consolidated by different blocks where they use cryptographic techniques (like hashing) to securely connect the chains in order to prevent the records from modifying, thus ensuring the integrity and immutability of data/information exchange. The data/information is transparent within the blockchain network, but data communication/modification requires cryptography for identity verification to protect the data security and privacy. Even so, blockchain needs AI technologies to efficiently process and analyze large volumes of data/information stored in blockchain.
Responsible AI (RAI) focuses on creating ethical guidelines for AI development, while explainable AI (XAI) aims to make AI models more understandable and interpretable. As a result, explainable AI can be viewed as a complementary component of responsible AI, playing a significant role in driving decision-making process.
As shown in the following figure, we explore the potential synergy between responsible/explainable AI and blockchain by mapping the intelligence cycle with the four key functions (Govern, Map, Measure, Manage) outlined in the AI risk management framework (RMF). Additionally, we examine how the interplay between AI and blockchain aligns with the principles of responsible and explainable AI.
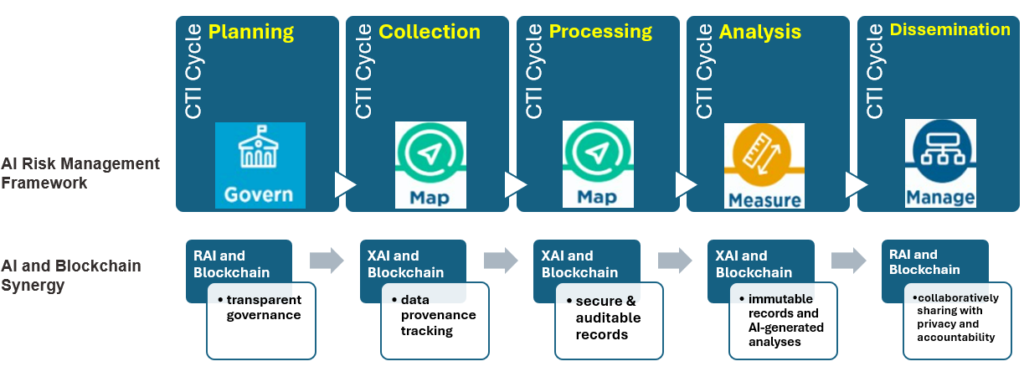
Blockchain and Responsible AI (RAI): Governing and sharing intelligence while maintaining security and privacy
Blockchain technology can significantly enhance responsible AI by building trust in AI applications through data integrity, security, transparency, and governance. It enables the creation of more diverse datasets for AI training through secure, decentralized data sharing. Blockchain technology can be leveraged to give individuals control over their personal data, allowing them to selectively share intelligence while maintaining privacy.
Blockchain and Explainable AI (XAI): Collecting tracible intelligence, processing intelligence content with AI/LLM, analyzing AI-generated insights
The integration of XAI and blockchain enables a more transparent and accountable approach to fraud detection, aiding in compliance efforts and reducing financial losses. Explainable AI is important because it allows users to understand why an AI model has made certain decisions, which can help them to trust the models and make better decisions. Blockchain can securely store and share CTI data, ensuring privacy and data integrity. XAI techniques can be employed to analyze this data and generate meaningful insights for intelligence professionals.
In essence, RAI and XAI play mutually supportive roles within the CTI cycle. The integration of RAI and XAI with blockchain technology could transform the CTI cycle, potentially enhancing trustworthiness, transparency, and effectiveness. As cyber threats continue to evolve, it will be imperative to explore how human-AI-blockchain collaboration can bolster CTI efforts.
Information Matters throughout the Intelligence Cycle
Within the National Initiative for Cybersecurity Education (NICE) Workforce Framework for Cybersecurity, a specific work role category known as “Cyberspace Intelligence” (CI) incorporates tasks associated with cyber threat intelligence. The professional in the CI work category “collects, processes, analyzes, and disseminates information from all sources of intelligence on foreign actors’ cyberspace programs, intentions, capabilities, research and development, and operational activities.” Information plays a crucial role in both CI and CTI. Information professionals who possess relevant expertise could make valuable contributions throughout the intelligence cycle.
This research has been partially funded by the U.S. Department of Homeland Security (DHS), Award Number 23STSLA00013.
Cite this article in APA as: Chang, H-C. & Lund, B. D. Bringing AI and blockchain synergy into cyber threat intelligence cycle. (2025, January 27). Information Matters, Vol. 5, Issue 1. https://informationmatters.org/2025/01/bringing-ai-and-blockchain-synergy-into-cyber-threat-intelligence-cycle/
Authors
-
Hsia-Ching (Carrie) Chang is an Associate Professor in the Department of Information Science, College of Information at UNT. She holds a Ph.D. in information science and an M.S. in information science from the State University of New York at Albany, as well as another M.S. in public policy from National Taipei University in Taiwan. She had industry experiences in business analytics, project management, secure software development, and digital marketing. She was a fellow in New America's Cybersecurity Initiative between 2018 and 2020. Her current research interests focus on cybersecurity education, AI-human collaboration/interaction, knowledge mapping, and emerging information systems/information technology adoptions.
View all posts -
Brady Lund, Ph.D., is an assistant professor of information science at the University of North Texas. His research examines critical factors at the intersections of information, data, technology and society, focusing particularly on the impact and policy implications of emerging data technologies on cultural practices and higher education contexts. Contributions to this research have been partially funded by the U.S. Department of Homeland Security (DHS), Award Number 23STSLA00013.
View all posts